HOME
Unveiling Hidden Patterns: Data Science in Forensic Investigations

Data science involves collecting, processing, and analyzing data to uncover patterns, trends, and correlations that can drive valuable business decisions and scientific discoveries. It encompasses a range of activities, including data cleaning, exploratory data analysis, feature engineering, machine learning model building, and deployment.
From optimizing marketing campaigns and improving healthcare outcomes to predicting stock market trends and enhancing customer experiences, data science empowers organizations to leverage data for strategic advantage. Enrolling in a great PG Course in Data Science can give individuals a new direction in their careers towards a data-driven future.
Data science plays a pivotal role in cybercrime detection, leveraging advanced techniques to analyze vast amounts of data and identify patterns indicative of malicious activities. Here’s an exploration of how data science is applied in this critical domain:
- Advanced Data Analysis: Data scientists utilize sophisticated algorithms to parse through massive datasets collected from various sources, such as network logs, user activity records, and transaction histories. By analyzing this data, they can uncover anomalies and potential threats that may indicate cyberattacks or unauthorized access attempts.
- Machine Learning Algorithms: Machine learning (ML) algorithms are employed to detect patterns in data that might not be apparent through traditional methods. For instance, anomaly detection algorithms can identify unusual behaviors or transactions that deviate from standard patterns, signaling potential security breaches.
- Behavioral Analysis: By establishing baseline behaviors and monitoring deviations, anomalies indicative of malicious intent can be detected early. This approach helps in preemptive threat mitigation and fraud prevention.
- Predictive Modeling: Predictive analytics models are developed to anticipate cyber threats based on historical data and ongoing trends. These models use statistical techniques to forecast potential attacks, allowing proactive measures to strengthen defenses and mitigate risks.
- Big Data Utilization: The volume, velocity, and variety of data generated in cyberspace require robust big data technologies for adequate storage, processing, and analysis. Data scientists employ scalable platforms and tools capable of handling large datasets to extract actionable insights promptly.
- Visualization and Reporting: Data visualization techniques understandably present complex findings. Visual analytics dashboards provide cybersecurity professionals with intuitive interfaces to monitor real-time threats and investigate incidents efficiently.
- Regulatory Compliance: Data science assists organizations in adhering to regulatory requirements by providing audit trails and compliance monitoring capabilities. This ensures that cybersecurity practices align with industry standards and legal frameworks.
Utilizing Big Data for Criminal Pattern Analysis
Utilizing big data for criminal pattern analysis represents a significant advancement in law enforcement and public safety efforts. Here’s an in-depth exploration of how big data is employed in analyzing criminal patterns:
- Data Aggregation and Integration: Law enforcement agencies gather crime reports, arrest records, surveillance footage, social media, and public databases. Big data technologies enable the aggregation and integration of these heterogeneous datasets into a centralized platform for comprehensive analysis.
- Pattern Recognition: Big data analytics employ sophisticated spatial and temporal analysis of crime incidents, criminals’ modus operandi, demographic trends, and socio-economic factors influencing criminal behavior.
- Predictive Policing: By leveraging historical crime data and real-time inputs, predictive analytics models can forecast where and when crimes are likely to occur. These models help law enforcement agencies allocate resources strategically, enhance patrol routes, and deploy personnel to prevent crimes proactively.
- Crime Hotspot Identification: Big data analytics enable the identification of crime hotspots—areas with high concentrations of criminal activities. This information allows law enforcement agencies to priorities their efforts in these regions, implement targeted interventions, and improve public safety.
- Supporting Investigations: Big data analytics provide valuable insights during criminal investigations by linking related incidents, identifying potential suspects through pattern recognition, and uncovering hidden connections that may not be apparent through traditional methods.
- Real-Time Monitoring and Response: Advanced analytics and real-time data processing enable law enforcement agencies to monitor events as they unfold. This capability facilitates rapid response to emergencies, mitigates risks, and enhances situational awareness in dynamic environments.
- Ethical and Legal Considerations: Despite its benefits, the use of big data in criminal pattern analysis raises ethical and legal considerations, including privacy concerns, data security, and ensuring transparency in decision-making processes.
In summary, utilizing big data for criminal pattern analysis revolutionizes law enforcement by enabling proactive strategies, enhancing investigative capabilities, and improving overall public safety. By harnessing the power of big data analytics, law enforcement agencies can stay ahead of criminal activities, optimize resource allocation, and ultimately create safer communities.
Machine Learning in Digital Forensics
Machine learning (ML) has emerged as a transformative tool in digital forensics, revolutionizing the investigation and analysis of digital evidence. Here’s an in-depth exploration of its application in this critical field:
- Automated Evidence Analysis: ML algorithms are employed to automate the analysis of digital evidence gathered from computers, mobile devices, and other digital sources. These algorithms can swiftly sift through vast amounts of data, identify relevant information such as timestamps, file metadata, and communication logs, and flag suspicious activities or anomalies.
- Malware Detection and Classification: ML techniques play a crucial role in detecting and classifying malware strains found on compromised devices. By analyzing patterns in code, behavior, and network traffic, ML models can identify malicious software, understand its capabilities, and provide insights into potential threats.
- Behavioral Analysis: ML-based behavioral analysis helps in understanding the actions and intentions of digital suspects. Algorithms can analyze user behaviors, interactions with digital systems, and deviations from standard patterns to detect unauthorized access, data exfiltration, or insider threats.
- Digital Image and Video Analysis: ML algorithms are utilized to analyze digital images and videos for forensic purposes. This includes identifying manipulated or edited content, extracting metadata, and even performing facial recognition to link individuals to digital evidence.
- Predictive Analytics for Incident Response: ML models can predict potential security incidents by analyzing historical data and patterns of cyber threats. This proactive approach enables digital forensics teams to prepare for and mitigate risks before they escalate.
- Challenges and Considerations: While ML enhances digital forensic capabilities, challenges include the need for extensive and diverse datasets to train robust models, ensure model interpretability, and address biases in data analysis. Moreover, maintaining the security and integrity of digital evidence throughout the ML process is critical to upholding its admissibility in legal proceedings.
- Future Directions: The future of ML in digital forensics lies in advancements such as explainable AI, which enhances transparency in decision-making processes, and federated learning, enabling collaborative analysis of distributed data without compromising privacy.
Conclusion
Predictive analytics empowers law enforcement agencies to adopt a proactive approach to crime prevention, leveraging data-driven insights to anticipate and mitigate criminal activities. By harnessing the power of predictive models, communities can enhance public safety, allocate resources effectively, and foster a more secure and resilient environment.
ML in digital forensics represents a paradigm shift, empowering investigators with efficient tools to uncover digital evidence, combat cybercrime, and ensure justice. As technology evolves, integrating a good PG Course in Data Science course can make individuals into digital forensic workflows, which will continue to strengthen investigative capabilities and enhance the resilience of digital infrastructures against evolving threats.
HOME
Giniä: Understanding Its Meaning and Relevance
Introduction
The word giniä is not widely recognized in mainstream English, but it resembles terms that may appear in linguistic, cultural, or conceptual contexts. While it is not a standard term in dictionaries or scientific literature, its usage or appearance could relate to specific brands, personal names, cultural references, or even creative designations. This article explores possible meanings and interpretations of giniä, its linguistic features, and potential relevance in modern discourse.
The Linguistic Structure of Giniä
Analyzing the Word Form
At a glance, giniä appears to be a word constructed with a base (gini) and a diacritic mark (ä). The umlaut (¨) over the letter “a” suggests that the term may be influenced by languages such as German, Finnish, Estonian, or Swedish, where vowels with diacritical marks carry specific phonetic meanings.
In those languages:
- Words ending in -ia or -iä can indicate feminine forms or pluralities
Thus, giniä may be phonetically pronounced as “gih-nee-ah” or “gih-nee-eh”, depending on the language base.
Possible Language Origins
The word could have origins or usages in:
- Finnish, where “-ä” endings are common in partitive cases
- German, where “ä” changes pronunciation and meaning
- Constructed or brand names, designed to sound elegant or international
The creative use of the umlaut also makes it popular in branding or artistic contexts to create a unique and stylized term.
Possible Interpretations of Giniä
Given the versatility of made-up or regionally adapted words, giniä might be interpreted in several plausible ways.
1. A Brand or Product Name
Many brands today create names that are memorable, global, and culturally neutral, using stylized characters to stand out. Giniä could be a brand name for:
- A cosmetic or skincare product emphasizing natural or luxurious qualities
- A fashion label aiming for a European aesthetic
- A digital app or startup in wellness, AI, or design
In this case, giniä serves as a trademark-friendly term, possibly linked to values like clarity, sophistication, or innovation.
2. A Personal or Fictional Name
The name Giniä may be used as a fictional character in literature, gaming, or storytelling. It evokes a futuristic or mythological tone, making it a strong candidate for:
- Science fiction or fantasy characters
- Virtual assistants or AI personas
- Protagonists in indie games or novels
It may also function as a given name in fictional or multicultural contexts.
3. Cultural or Artistic Symbol
If giniä is used in an artistic context, it might represent a concept or idea. Artists, musicians, and designers sometimes invent names to signify a project or movement. For instance, giniä could be:
- A term representing feminine energy or intuition
- A symbol in abstract visual art
This type of name is designed to evoke emotion or provoke curiosity.
How Giniä Could Be Used in Business or Design
Branding Potential
One of the key attractions of the term giniä is its international appeal and visual uniqueness. The use of the diacritic makes it stand out in digital and printed formats. It’s short, easy to remember, and not tied to any specific known word, which makes it versatile in:
- Global brand naming
- Luxury product lines
- Minimalist or Nordic-inspired visual identities
Domain and Trademark Availability
Because it is an uncommon term, giniä may still be available as a domain name or trademark, making it ideal for startups looking for a unique brand presence online. Names like giniä.com or giniä.app would be desirable for companies focused on elegance, clarity, or simplicity.
Logo and Visual Representation
The shape and balance of the word “giniä” allow for strong visual design. Brands using it could emphasize clean lines, modern fonts, and stylish colors, consistent with Scandinavian, German, or Japanese minimalism.
Giniä in the Context of Language Creation
Some modern authors and game developers engage in conlanging—the creation of fictional languages. Words like giniä may originate in:
- Constructed language dictionaries
- Role-playing worlds
- Digital environments or metaverses
These invented words follow consistent grammar rules and often gain popularity through cultural adoption or viral storytelling.
Why Words Like Giniä Matter
Terms like giniä, while not yet defined by global consensus, reflect key trends in:
- Creative branding
- Multicultural fusion
- Phonetic aesthetics
- Digital identity
Understanding how and why such words emerge helps linguists, marketers, and content creators stay ahead of language evolution and cultural branding.
Conclusion
Though giniä does not yet have a universally accepted definition, it holds promise as a creative, flexible, and globally appealing term. Whether it becomes a brand name, a fictional character, or a linguistic innovation, giniä demonstrates the power of constructed vocabulary in a connected, creative world.
HOME
Transform Your Backyard into a Relaxation Oasis

Envision stepping out into your backyard and being instantly transported to a serene retreat, a space that feels like an escape just steps away from your door. With a bit of thoughtful planning and inspiration, turning your outdoor area into a personal sanctuary is easier than you may imagine. Whether you seek a tranquil spot to unwind after a long day or an inviting area to gather with friends, the process begins with purposeful design and a clear vision. For those considering water features or luxury enhancements, expert pool design and planning Orange County can be an integral part of achieving your oasis dreams.
Transforming your backyard is not only about adding furniture or plants. It’s about curating a setting that supports your lifestyle and brings you a sense of peace. Consider the moods you want to evoke and the functional needs you have. The right changes will make your space both attractive and deeply relaxing, while also adding value to your home.
When planning your backyard oasis, start by establishing zones for different uses, such as a dining area, a restful nook with a hammock, or a place for meditation. Layering in elements like greenery, soothing sounds, and comfortable furnishings turns an average backyard into a daily retreat. Small details, like the sound of water or the glow from ambient lighting, can make a significant difference.
Define Your Space
Begin by evaluating your backyard’s layout and dimensions. Clearly identifying distinct zones for lounging, dining, or quiet reflection enables multifunctional use without clutter. Use outdoor rugs, tall planters, or garden screens to discreetly segment areas. Creating these visual and physical boundaries can provide purpose while making even small yards feel spacious and organized. This intentional layout not only facilitates relaxation but also maximizes every square foot of your outdoor space.
Incorporate Comfortable Seating
Selecting the right outdoor furniture is essential for relaxation. Opt for weatherproof materials such as teak, powder-coated metals, or all-weather wicker to ensure longevity with minimal maintenance. Plush cushions, ottomans, and hammocks can elevate the comfort level and encourage long hours spent outdoors. Arrange seating in conversational groupings or create a solitary retreat with a hanging chair or daybed for reading and reflection. When possible, invest in modular seating that can be rearranged to accommodate gatherings or intimate moments alone.
Add a Water Feature
The gentle sound of flowing water has a remarkably calming effect and helps mask neighborhood noise. Installing a water element, such as a fountain, small pond, or sleek wall-mounted waterfall, can become a soothing focal point in your landscape. Water features also entice songbirds, butterflies, and other wildlife, enhancing your connection to nature and offering a multi-sensory relaxation experience. Gardening Know How suggests that even a compact feature, like a tabletop fountain, can dramatically transform the ambience.
Install Ambient Lighting
Lighting sets the ultimate mood for outdoor relaxation, extending your enjoyment well after sunset. String lights overhead, solar-powered lanterns hung in trees, and low-voltage path lights all contribute to a soft, inviting glow. Consider layering different light sources to highlight landscape features, illuminate pathways, or cast a gentle shimmer on water. Smart lighting systems that integrate with your devices add convenience, allowing you to personalize brightness and color for any occasion. According to Redfin, proper lighting brings warmth and safety while emphasizing the architectural beauty of your space.
Introduce Lush Greenery
Greenery introduces life, color, and a sense of tranquility to any yard. Select a variety of native plants, flowering shrubs, or ornamental grasses suited to your climate for easy maintenance and year-round interest. Position potted plants along walkways or patios, and tuck fragrant herbs near lounge areas for added sensory appeal. Planting layers, such as groundcover under taller bushes and trees, creates depth within the landscape. Incorporate evergreens for year-round color and prioritize pollinator-friendly flowers to support local ecosystems.
Create Shade
Shade transforms a hot, sun-drenched space into a comfortable haven. Start with classic options like umbrellas, canopies, or shade sails for easy versatility. For a more permanent resort-style feel, install structures such as pergolas or gazebos, draped with breezy outdoor fabric. You can also foster natural shade by training flowering vines on trellises or planting fast-growing shade trees tailored to your region’s conditions. Well-placed shade not only cools the area but also protects furnishings, prolonging their lifespan.
Add a Fire Feature
Fire features add warmth, ambiance, and a striking focal point to outdoor living areas. Freestanding fire pits, sleek fire bowls, and built-in fireplaces provide gathering spots for chilly evenings or lively get-togethers. Select a design that complements your landscape aesthetic and ensure it meets local safety regulations. Fire features can double as cooking areas for roasting treats or simply create a mesmerizing glow that invites relaxation and conversation well into the night.
Personalize Your Space
Infuse your backyard oasis with personal touches that showcase your style and passions. Outdoor art, decorative throw pillows, wind chimes, or a miniature herb garden can define the space as uniquely yours. Incorporate family heirlooms, travel finds, or hand-crafted decor to create an outdoor area that feels like an extension of your home. Personalization deepens your connection to the environment, making your backyard a welcoming retreat for both peaceful solitude and joyful gatherings.
Final Thoughts
Crafting a backyard oasis involves careful planning, creative touches, and an emphasis on comfort and natural beauty. By considering function, aesthetics, and seasonal adaptability, you can create a personalized retreat that offers daily renewal and lasting value.
HOME
Innovative Applications of Meteorological Towers in Renewable Energy
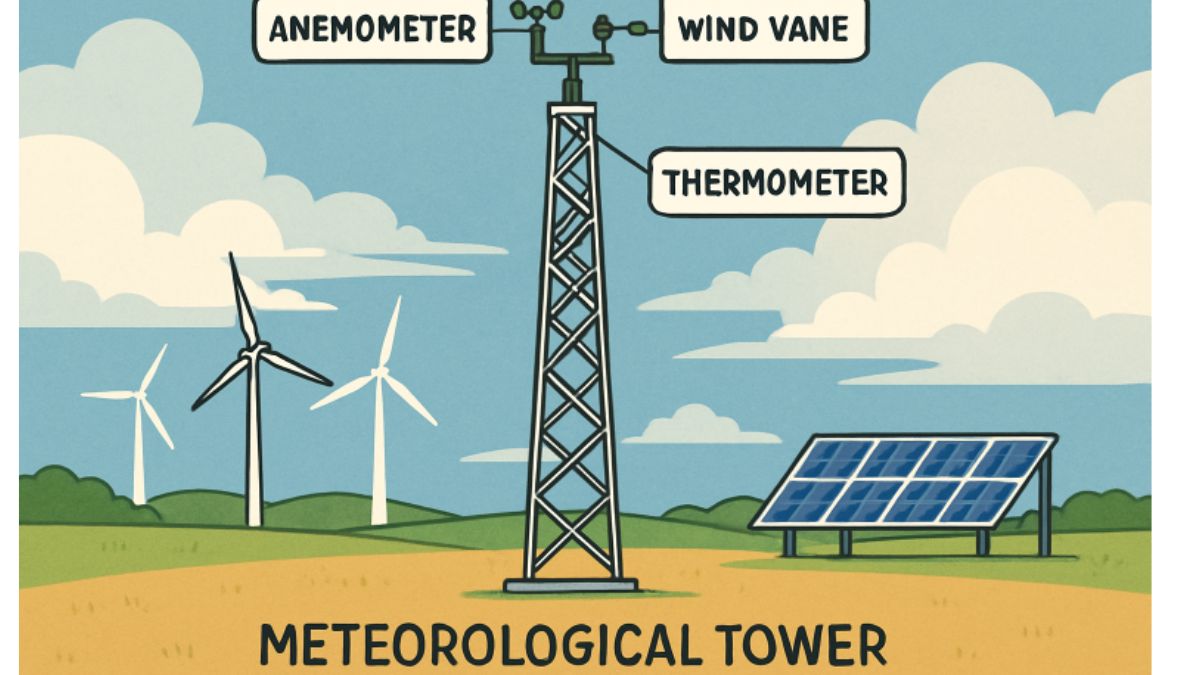
Meteorological towers, also known as met towers, play an integral role in the development and enhancement of renewable energy projects. These towers are installed to collect accurate meteorological data, which is fundamental for evaluating wind energy potential. For organizations and project developers seeking to optimize renewable energy sites, successful meteorological tower installation can be the critical step between feasibility study and profitable energy production.
The value of these towers extends beyond simply measuring wind speed. They gather comprehensive profiles of atmospheric conditions, including wind direction, air pressure, temperature, and humidity, which contribute to the reliability and efficiency of wind energy systems. With increased demand for sustainable energy sources, the technical and strategic placement of met towers has become a focus of innovation.
Recent years have seen remarkable growth in the use of met towers not only for conventional wind farm planning but also for newer, diversified applications. As climate targets tighten and investment in renewables expands, innovative approaches to harnessing wind and solar power have surfaced. This has driven advances not just in turbine technology but also in the structures that support and inform them.
Beyond wind assessment, meteorological towers have begun to integrate with various renewable energy systems. As global leaders invest in greener infrastructure and urban environments become more energy-conscious, the design and implementation of these towers continue to evolve into addressing novel environmental and operational challenges.
Role of Meteorological Towers in Wind Energy
Meteorological towers are foundational for wind energy project development. By delivering real-time, precise data on wind speed and variability, they enable site developers to assess the quality and consistency of wind resources at prospective turbine locations. This influences every stage of a wind project, from the initial feasibility study and turbine selection to site layout and ongoing performance monitoring. Data accuracy impacts millions in investment and long-term reliability, making these towers a necessity for energy companies and engineers alike. For a thorough review of modern wind data methodologies, see how the U.S. Department of Energy evaluates wind resource measurement.
Advancements in Meteorological Tower Design
Innovation is reshaping how meteorological towers are designed and utilized. Novel concepts, such as vortex engines, are being explored to reimagine traditional infrastructure models. These systems replace tall chimneys with engineered air vortices that replicate natural weather phenomena to lift warm air and generate mechanical energy with a fraction of the footprint. In addition, advances in sensor technology and data transmission enable real-time, remote analytics, increasing the precision and usefulness of data collected by towers in challenging environments.
Sustainability is also driving change in design philosophy. The use of renewable construction materials, modular assembly techniques, and adaptive structural forms all point to a greener, more cost-effective future for meteorological towers in renewable applications.
Integration with Solar Energy Systems
The integration of meteorological towers with solar energy infrastructure marks a significant leap in the efficiency of renewable energy systems. Facilities such as the RayGen PV-Ultra Thermal-Hydro Storage Power Plant in Victoria, Australia, combine high-performance solar arrays with advanced energy storage to deliver grid-stabilizing, dispatchable energy. Here, meteorological towers continuously monitor wind and solar conditions, providing the data needed to fine-tune operational strategies and maximize output. Developments like these are a testament to the growing importance of precise weather data for all forms of renewables. Significant industry insights can be found in PV Magazine’s coverage of Australia’s pioneering solar-hydro storage project.
Urban Applications of Meteorological Towers
Urban centers present unique challenges and opportunities for renewable energy deployment. Traditional wind turbines, with their large blades and space requirements, are often unsuitable for densely populated areas. Here, meteorological towers are supporting innovations such as vortex bladeless wind turbines. These compact, oscillating structures harness wind energy silently and efficiently, making them ideal for rooftop or compact city installations. By equipping these urban turbines with networked meteorological towers, cities can gain valuable insights into microclimates and optimize the integration of renewable energy into municipal buildings and infrastructure.
Case Study: The World’s Largest Wooden Wind Turbine Tower
The inauguration of the world’s tallest wooden wind turbine tower in Skara, Sweden, in March 2024 marked a new chapter in sustainable engineering. At 103 meters tall, this structure supports a Vestas V90-2.0 MW turbine and is constructed predominantly from locally sourced wood laminates. This project not only reduces the tower’s carbon footprint but also showcases how renewable materials can facilitate taller, more productive installations. The design supports greater wind harvesting capabilities while offering a model for future eco-conscious construction in the wind sector.
Future Prospects and Challenges
The continual evolution in the applications of meteorological towers highlights both remarkable opportunities and emerging challenges. While innovations in materials, analytics, and integration pave the way for enhanced sustainability and efficiency, barriers such as high upfront investment, technical skill requirements, and regulatory complexity must be overcome. Environmental considerations, particularly for sensitive sites, demand ongoing research into lighter, more adaptable structures.
Looking Ahead
Expanding the role of meteorological towers in hybrid renewable grids, smart cities, and offshore installations remains a top priority for global clean energy initiatives. As research and cross-industry collaboration intensify, these towers are poised to become an even greater asset in the transition toward a resilient, low-carbon future. The advances being made today will serve as the foundation for the energy solutions of tomorrow.
-

 HEALTH2 years ago
HEALTH2 years agoIntegrating Semaglutide into Your Weight Loss Plan: A Practical Guide
-

 HOME IMPROVEMENT2 years ago
HOME IMPROVEMENT2 years agoHow to Choose the Perfect Neutral Area Rug for Every Room
-

 FASHION2 years ago
FASHION2 years ago7 Celebrity-Inspired Elegant Summer Dresses For 2024
-

 LAW2 years ago
LAW2 years agoTeenage Drivers and Car Accidents in California: Risks and Parental Liability
-

 CONSTRUCTION2 years ago
CONSTRUCTION2 years agoConstruction Site Safety Regulations in New York and Your Rights as a Worker
-

 LAW2 years ago
LAW2 years agoPost-Divorce Considerations in California: Modifications and Long-Term Planning
-

 HOME2 years ago
HOME2 years agoSandra Orlow: The Teen Model Who Captivated the Internet
-

 FINANCE2 years ago
FINANCE2 years agoDigital Asset Management in Florida Estate Planning
